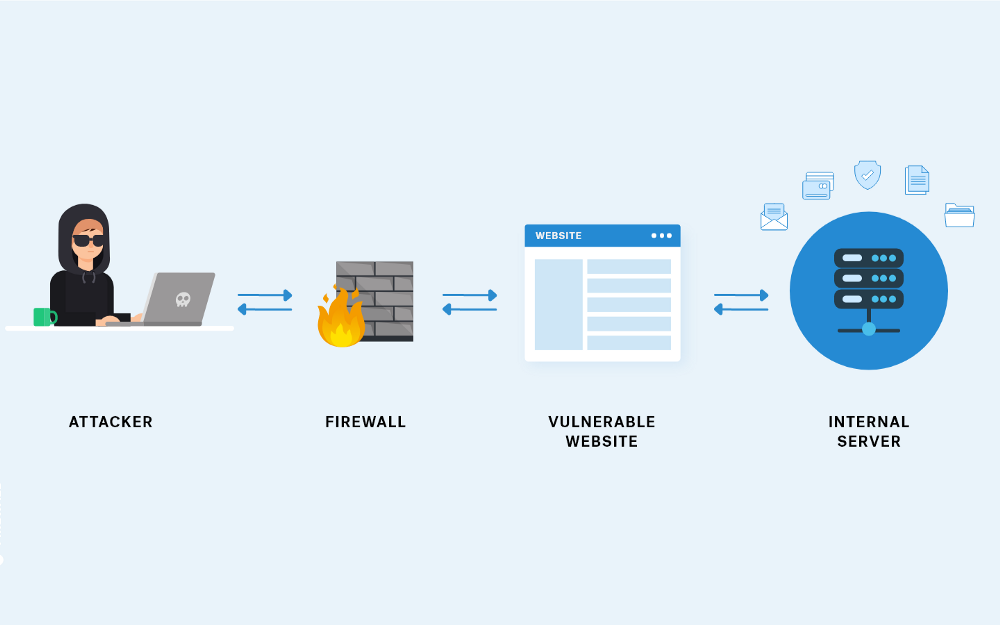
A company is only as secure as its software. Any time a business introduces new technology into operations, sensitive information must be secured with respect to the additional level of risk the new components pose to the entire system. A common method information security specialists use for this process is the Common Vulnerability Scoring System (CVSS).
The Common Vulnerability Scoring System offers a method of assessing how vulnerable software is to attack. Many cybersecurity professionals use the CVSS base score as a primary metric to determine the severity of an exploitable weakness. This framework helps businesses ensure confidentiality integrity with regards to their customer's sensitive data.
With that in mind, we’re going to provide an overview of CVSS V3 and look closely at how the rating system helps businesses properly allocate resources to cybersecurity.
What is a CVSS Base Score?
CVSS is a framework used to rank the characteristics and severity of a software’s exploitable weaknesses. This system creates a Base Score that rates a vulnerability between 0 and 10 depending on severity. The groups consist of:
- Base
- Temporal
- Environmental metrics
We’ll dive into these metrics in a little more detail below, but first, let’s explore the overall methodology to gain a better understanding of the broader concepts here.
Vulnerability Scoring System: CVSS Rating Methodology
The scoring system provides a simple and straightforward numeric system for establishing the potential threat individual components pose to a system.
The Base Score breakdown includes:
- 0.0 = No threat to the system
- 0.1-3.9 = Low
- 4.0-6.8 = Medium
- 7.0-8.9 = High
- 9.0 - 10.0 = Critical
The lower the score, the less risky the vulnerability poses to the entire system, whereas a 10.0 score needs to be addressed immediately.
Components of CVSS Score Methodology
A US-based non-profit organization, FIRST produces the CVSS methodology, with the latest iteration being version 3.1. The core metric here, called the Base, can be impacted by the Temporal and Environmental metrics results.
The base metrics are compiled to create a universal standard that can function across industry boundaries. A CVSS Base Score utilizes a vector string to accomplish this which is a dynamic array that provides accurate and consistent vulnerability severity scores.
Cybersecurity practitioners utilizing this framework to evaluate a system will provide the Base score, and if necessary, the Temporal score. Afterwhich, the final decision rests with the end-user to calculate and integrate the Environmental Score, based upon environmental factors unique to the business and system.
Base Score
The base score operates using a 0 to 10 scale attributed to inherent vulnerabilities of software unaffected by time or environmental factors. The CVSS Base Score includes two subscores, Exploitability and Impact.
Understanding the underlying definitions and the other broader definitions can help security practitioners and business operators gain a better understanding of this framework.
Exploitability Subscore
The Exploitability Subscore is derived from the aspects of the individual vulnerable component. The easier that the component is to attack, the higher the CVSS v3 severity levels score it. The metrics used to determine the
Exploitability Subscore include:
Attack Vector (AV) — ranks how difficult it is for hackers to target the vulnerability.
Attack Complexity (AC) — ranks the environment that a hacker must overcome to attack the vulnerability.
Privileges Required (PR) — ranks the level of credential access a hacker must use to exploit the vulnerability.
User Interaction (UI) — ranks how difficult a target is to hack unaided by additional users.
Impact Subscore
The Impact Subscore is used to determine the severity of vulnerable individual components in a successful attack. The metrics used to calculate the Impact Subscore include:
Authorization Scope (S) — ranks the degree of impact a component can have on other parts of the system.
Confidentiality (C) — ranks the level of authority that an exploit lends to the attacker.
Integrity (I) — ranks the degree of corruptible or modifiable data offered by an exploit.
Availability (A) — ranks the loss of availability to an exploitable resource.
CVSS Base Score vs. Temporal Score: What’s the Difference?
The CVSS lists detailed information about a vulnerability’s impact on affected systems. However, for companies to learn how to prioritize software vulnerabilities, they will need to calculate the CVSS v3 score before taking into account environmental factors. This ranking calculation includes the Base Score with a modification to it by the Temporal Score.
Temporal Score
The Temporal Score will impact the metrics used to determine the CVSS Base Score. This score composition includes three metrics:
The Exploit Code Maturity (E) — ranks the likelihood that an exploit will be leveraged based on existing scripts found on the Internet.
Remediation Level (RL) — ranks the ease that an exploit can be remediated.
Report Confidence (RC) — ranks the reliability that a vulnerability exists.
Benefits of Using the CVSS Scoring System
A primary benefit of using the CVSS scoring system aims to provide a universal framework that all industries can use to gauge the severity of cybersecurity vulnerabilities.
Common practice should allow for each solution provider to use its own scoring method. However, without a consistent baseline, system administrators previously had to juggle multiple solution approaches to determine which vulnerability should be a remediation priority.
With the development of the CVSS scoring system, cybersecurity teams and IT service providers can use this open framework to assess any IT environment. This means that private businesses, organizations, and governments can rely on information security professionals to register the impact of exploits within their systems and rank them by severity more consistently, regardless of industry.
A secondary benefit of adopting the CVSS scoring system derives from companies having a standardized formula that allows organizations to meet the security regulations imposed on their specific sector. Most compliance frameworks also require a standard ranking system like the CVSS system for ranking and categorizing vulnerabilities, so using CVSS may get you credit in your compliance programs as well.
Contact Cobalt & Learn the Benefits of a Pentesting Program
If you want to ensure that your security systems have been properly tested, schedule a demo penetration test today with Cobalt. Our team of experts can improve your systems’ CVSS Base Score by helping to identify, track, and remediate any vulnerabilities that threaten your business.
Finally, learn more about the topic of how pentesting relates to risk management with expert insights.